cIFrex 5.0 - Static code analysis tool
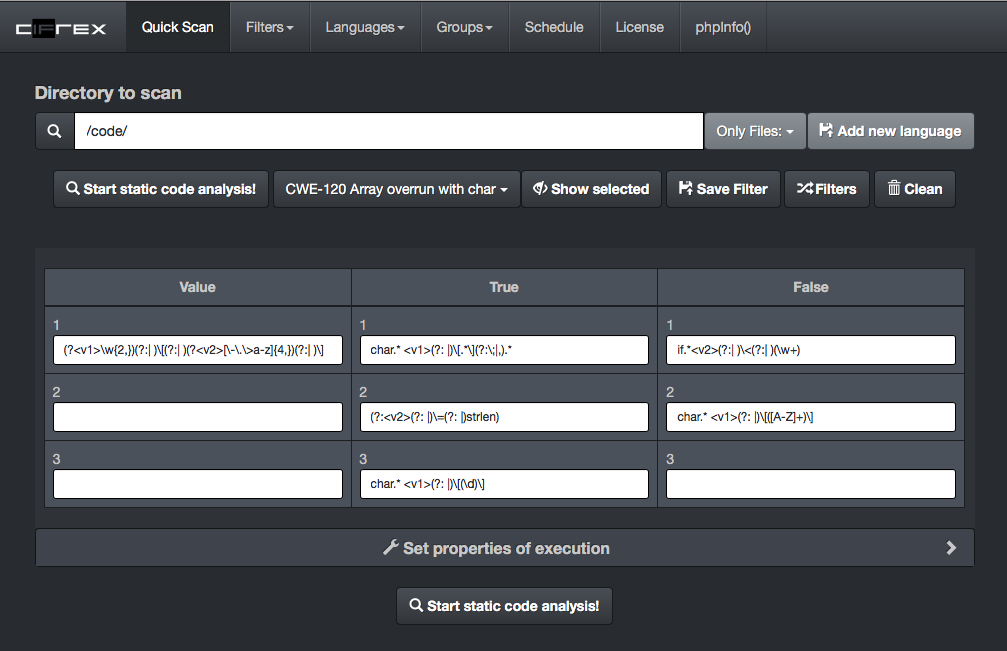 |
cIFrex is an security tool, which supports search for mistakes in the source code during static code analysis. Using the database of filters based on regular expressions, you can quickly locating the code, in which the probability of failure is high. To be able to use cIFrex search, you should have basic knowlage about regular expressions and static code review. This tool facilitates static code analysis during security audits or finding malicious code by using regular expressions. Some functions in the code may generate a risk, such as for PHP and disable_functions. Do you want to know if any of these features were used in your code? Try cifrex. Supported OS: Linux Centos Ubuntu macOS Dependencies: Docker Bash Mariadb |
Installation and system requirements
To install cifrex use
# sh ./install.sh
if success use login: cifrex pass: cifrex
http://127.0.0.1:3380/
To start cifrex use
# sh ./start.sh
To stop cifrex use
# sh ./stop.sh
To remove cifrex use
# sh ./remove.sh
To export cifrex DB use
# sh ./exportdb.sh
you can change the configuration in your 'CONFIGURATION' file
######################################
### WEBSERVER DOCKER CONFIGURATION ###
######################################
# BIND CIFREX SERVICE ON HOST AND PORT
IP_HTTP=127.0.0.1
PORT_HTTP=3380
PORT_HTTPS=33443
# BASIC AUTHORIZATION, YOU CAN CREATE MORE USERS AFTER INSTALATION
HTTP_USER="cifrex"
HTTP_PASS="cifrex"
######################################
### WEBSERVER DOCKER CONFIGURATION ###
######################################
# CREATE DOCKER CONTAINER FOR DATABASE
USE_DOCKER_DB=true
# IMPORT DEFAULT DB AND THE LATEST.SQL
IMPORT_DEFAULT_DB=true
# EXPORT DB TO DBDumps DIRECTORY
EXPORT_DB_EVERY_60SEC=true
# BIND OR USE IP AND PORT FOR DB
IP_DB=127.0.0.1
PORT_DB=33306
# SET DOCKER DB PASSWORD WHEN USE_DOCKER_DB=true
DB_ROOT_PASS="ChangEth1sP455wOrDnow"
|
edit src/config*.php files to customize the DB connection and other PHP settings
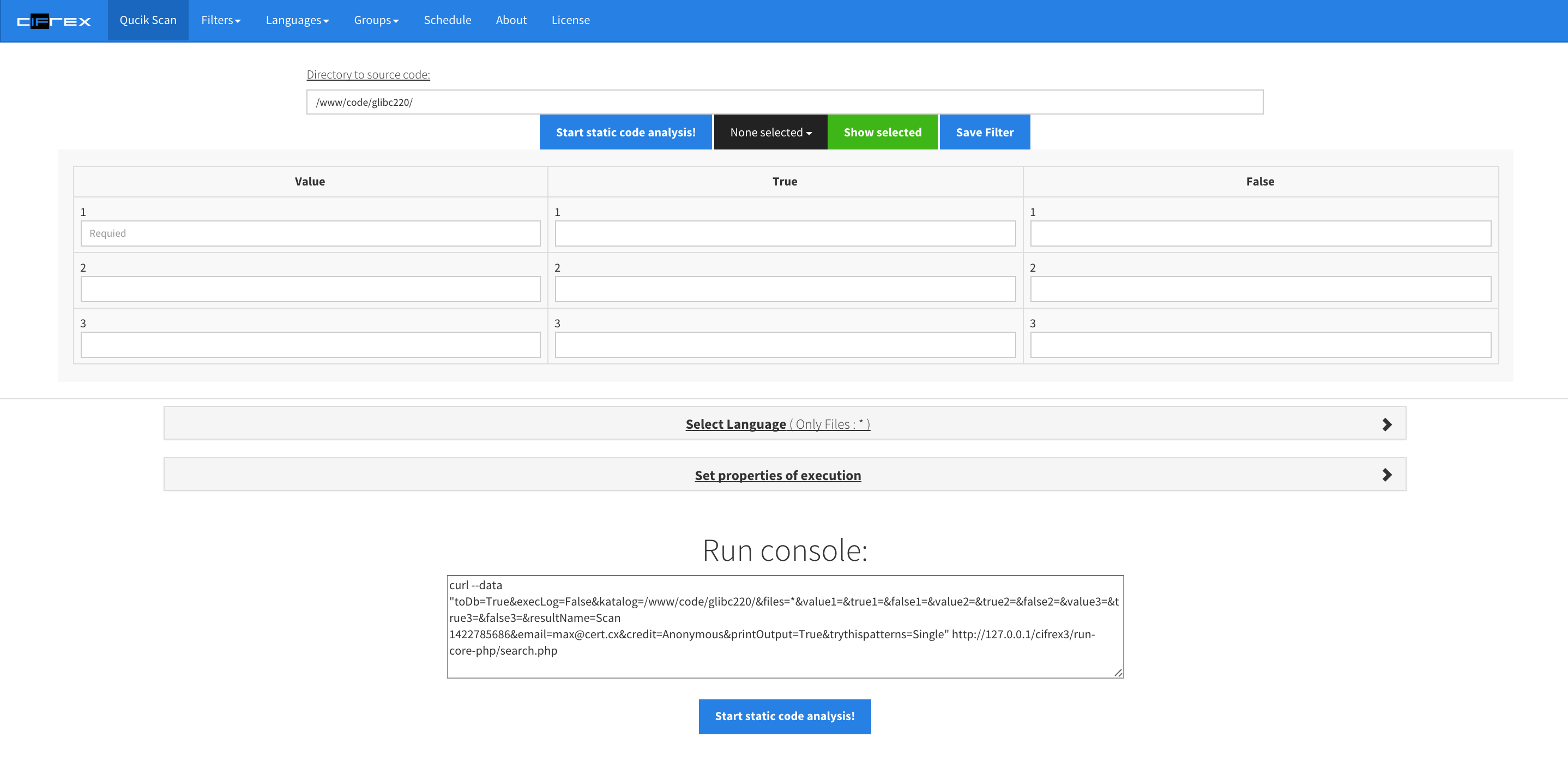
How to use?
cIFrex filters are based on regular expressions, describing given kind of mistake together with the resources like CWE identifiers, OWASP. This enables you to reach a lexical definition at http://cwe.mitre.org fast.
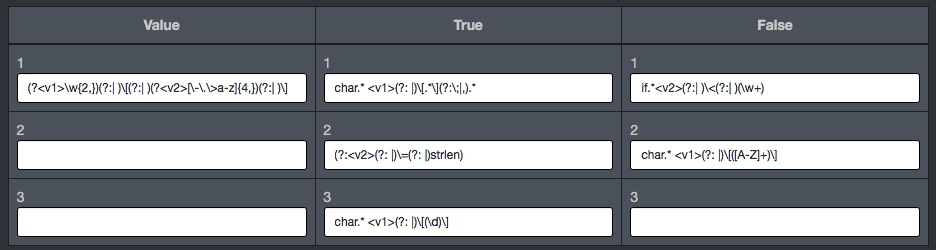
- (V) Value: Regular expression enabling retrieval of the sequences of signs and the attribution of retrieved values to the variable <v1>, <v2> lub <v3> for example the name of array:
char name[128] => char.* (?<v1>\w+)\[(\d+)\]
It allows us to use found values in the patterns of type T (Truth) and F (False).
- (T) Truth: Regular expression, which must be present in the code. for example:
strcpy\(<v1>\,
- (F) False: Regular expression, which cannot be present in the code. for example:
if.*(?:.\=\=.NULL|NULL.\=\=.)
Each expression fulfils given roles. The expressions of type (V) are used mainly to assign the variable names while the expression of type (T) and (F) are mainly used to precise their usage. To put it simply, patterns of type V are used to catch names of variables, used in the unsuitable manner, for example all arrays (<V1>) of type CHAR used in the function strcpy()(<T1>) without controlling the length through strlen()(<F1>).
It is possible to change default directory by setting $default_directory in the code of cIFrex.
Which means the localization of the analyzed source code.
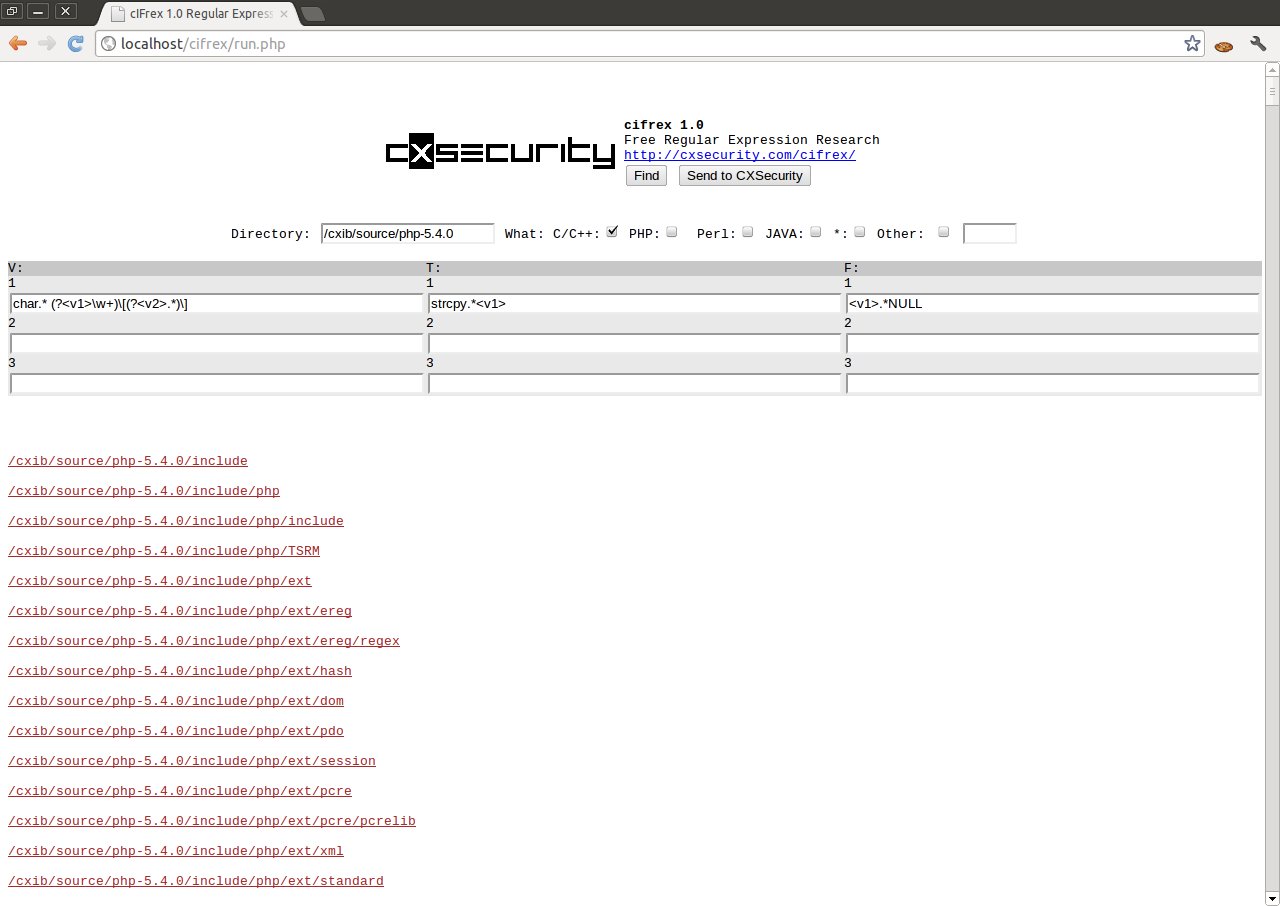
By using three types regular expressions, we can create a filter which will be checked in all indicated files. If all expressions will be fulfilled, file will be shown in the search results. This does not mean, that it is susceptible to the given mistake. The efficiency of the method can oscillate on the level several percent, depending on the filter exactness. More details in the regular expressions gives us the larger probability of finding the error.
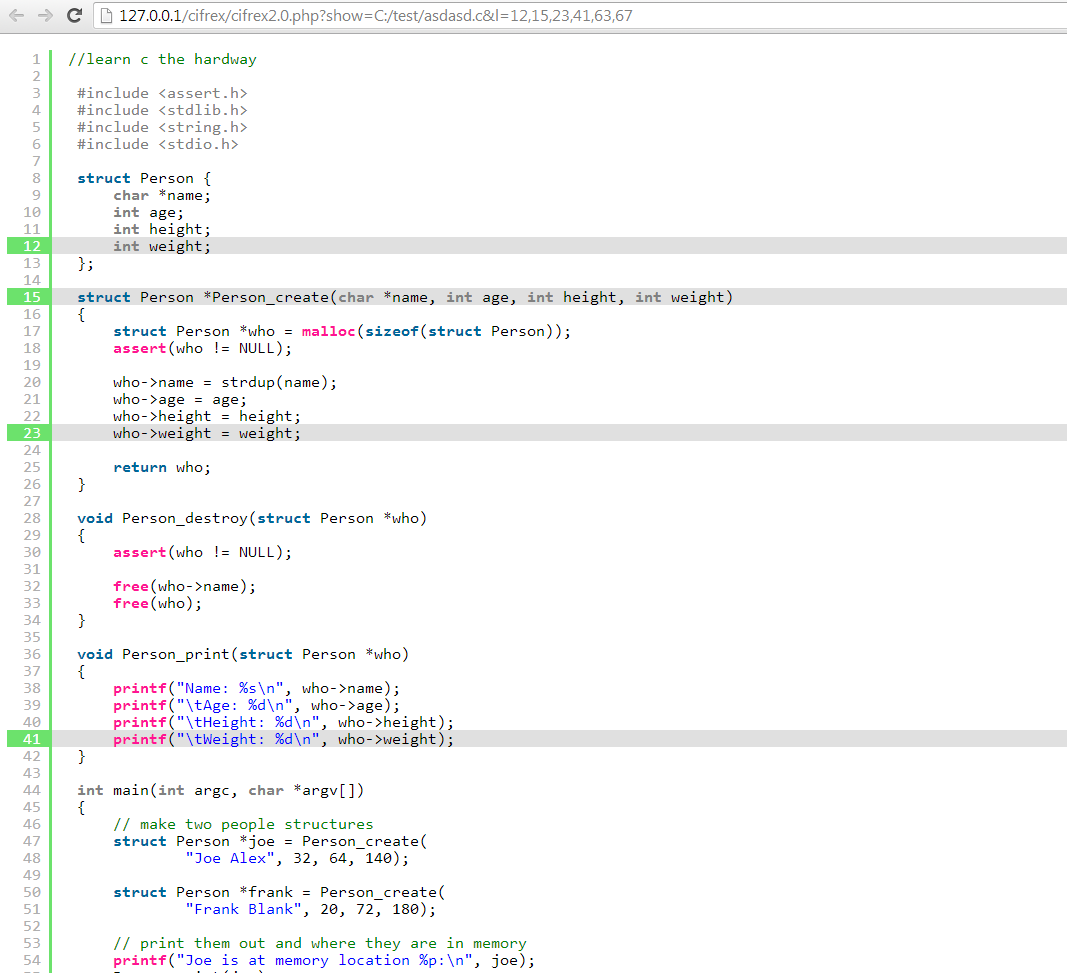
Let us analyse thoroughly after-mentioned example. It try find name and size of CHAR Table through the pattern: V1
char.* (?<v1>\w+)\[(?<v2>.*)\]
Thanks to the application of variables <v1> and <v2>, we can dynamically find the name of table and its size. This can help us in the creation of succeeding regular expressions of type T and F. In this case, the expression of type T1 is:
(.*strcpy\(<v1>\,.*)
If in the given file will be found line with use of strcpy() function and the name <v1> condition will be fulfilled. In contrast to the conditions of type F, which are fulfilled in the situation when a given expression does not appear in the code. For example use of array name <v1> and the string NULL <v1>.*NULL in one line.
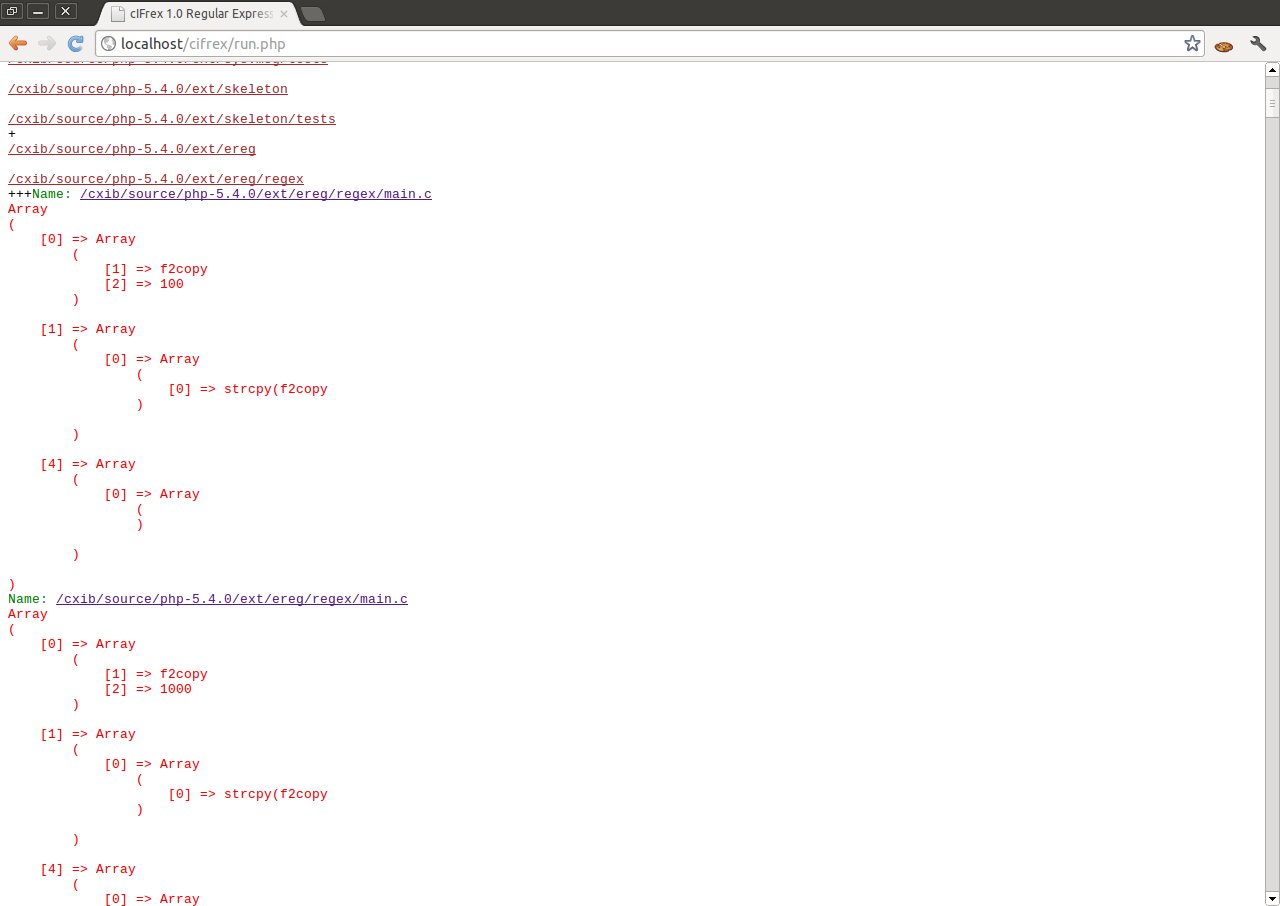
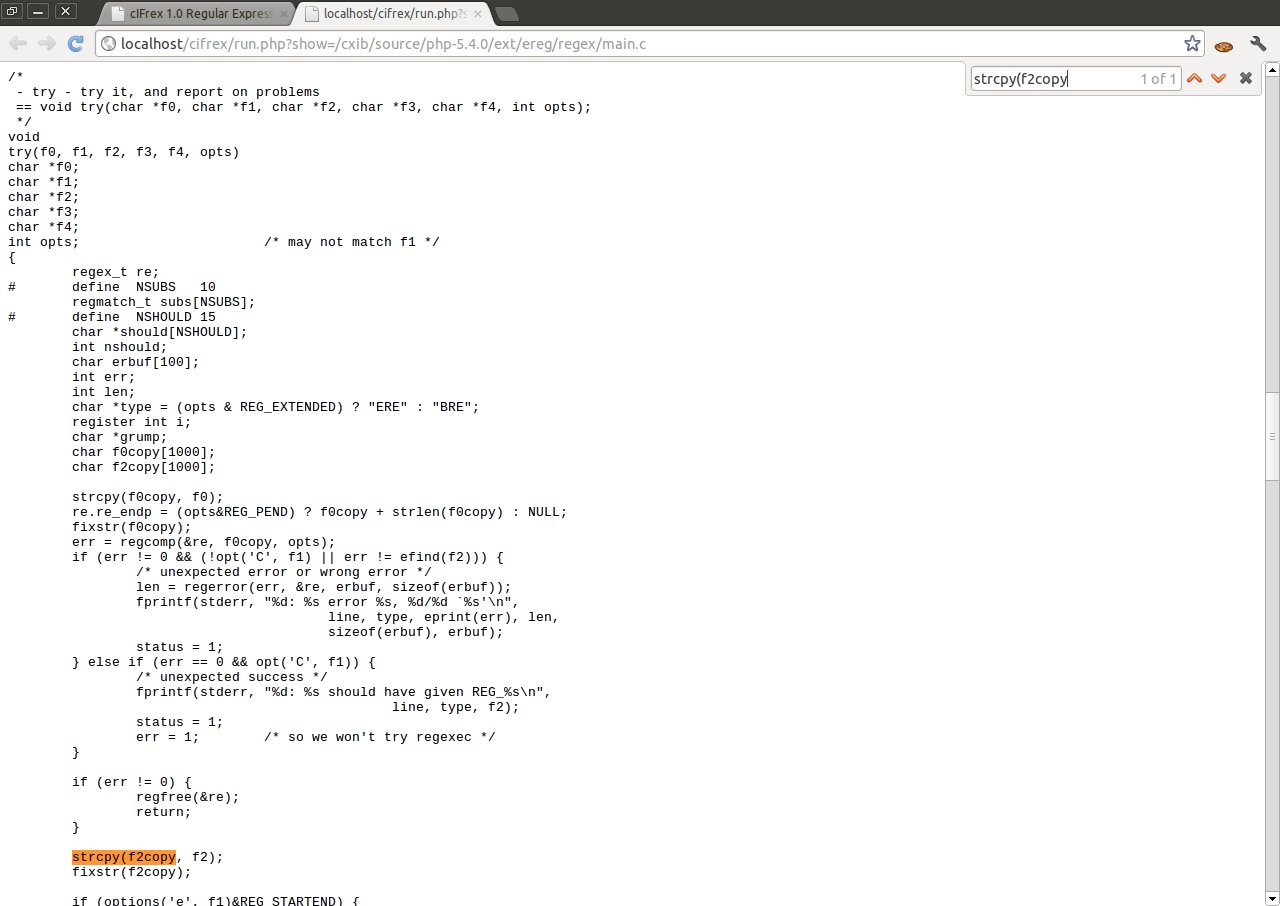
It can be seen in the after-mentioned example, that cIFrex helped us to find the use of function strcpy () in the risky manner. Copying the indicator f2 to the board f2copy [1000] without controlling its length, can show in the large degree the appearance of mistake. cIFrex does not state that the error has occurred, but only helps in finding the risky programmers behaviours.
Another example of cIFrex use is the search of dangerous use of function malloc (), realloc () or calloc (). As we know, each of these functions when lacking the possibility of the allocation of a given data block, returns NULL. If we do not control returned values we can cause NULL pointer dereference error to occur.
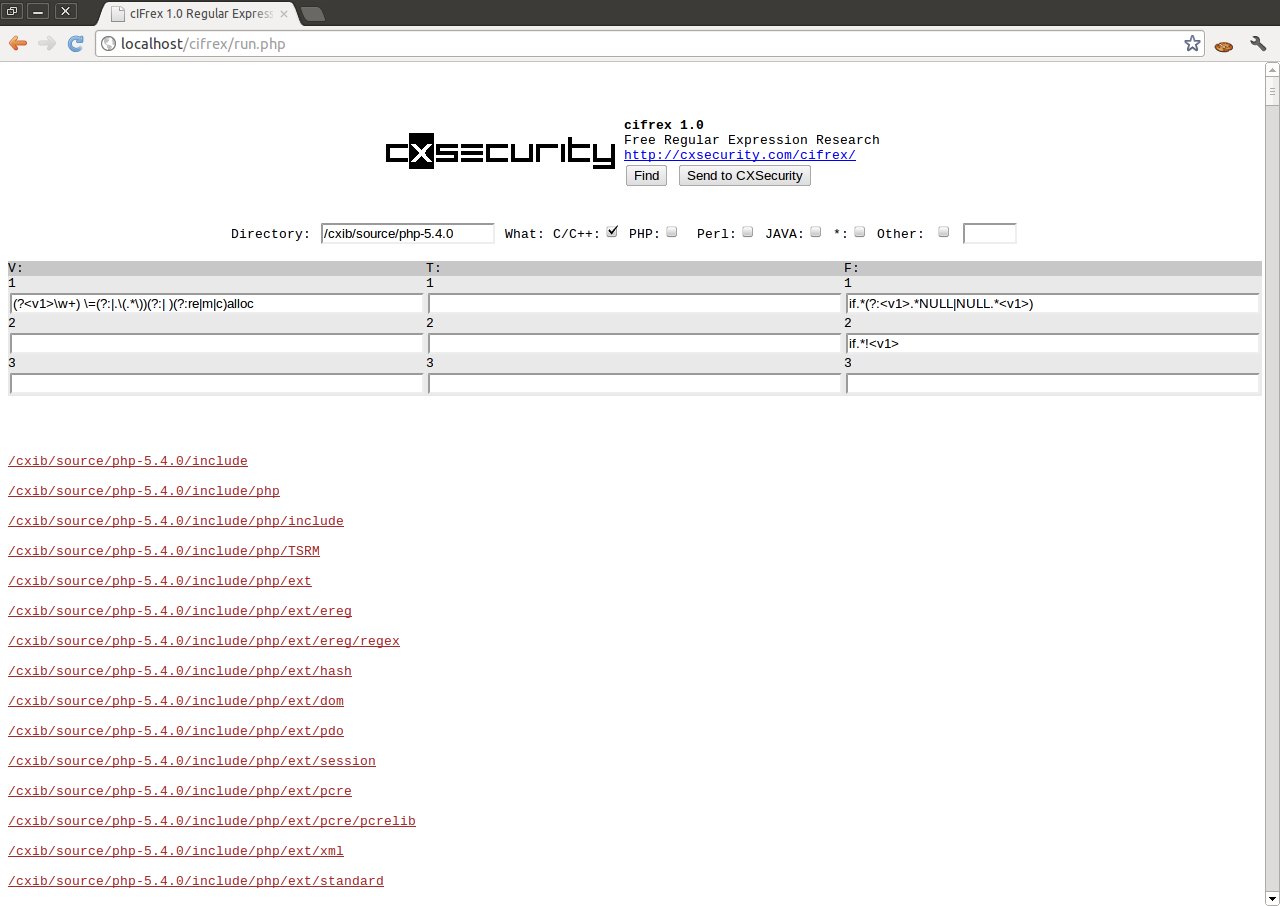
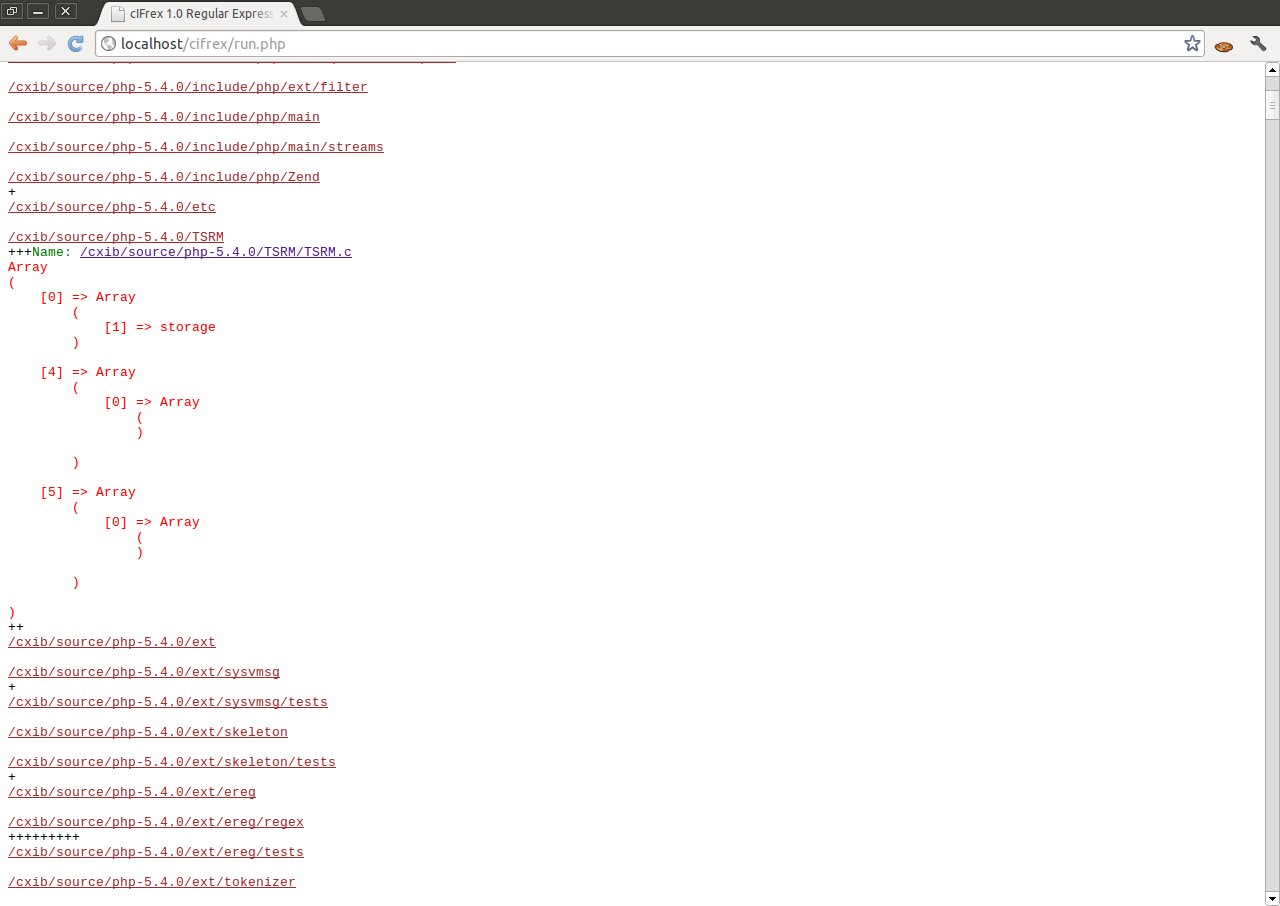
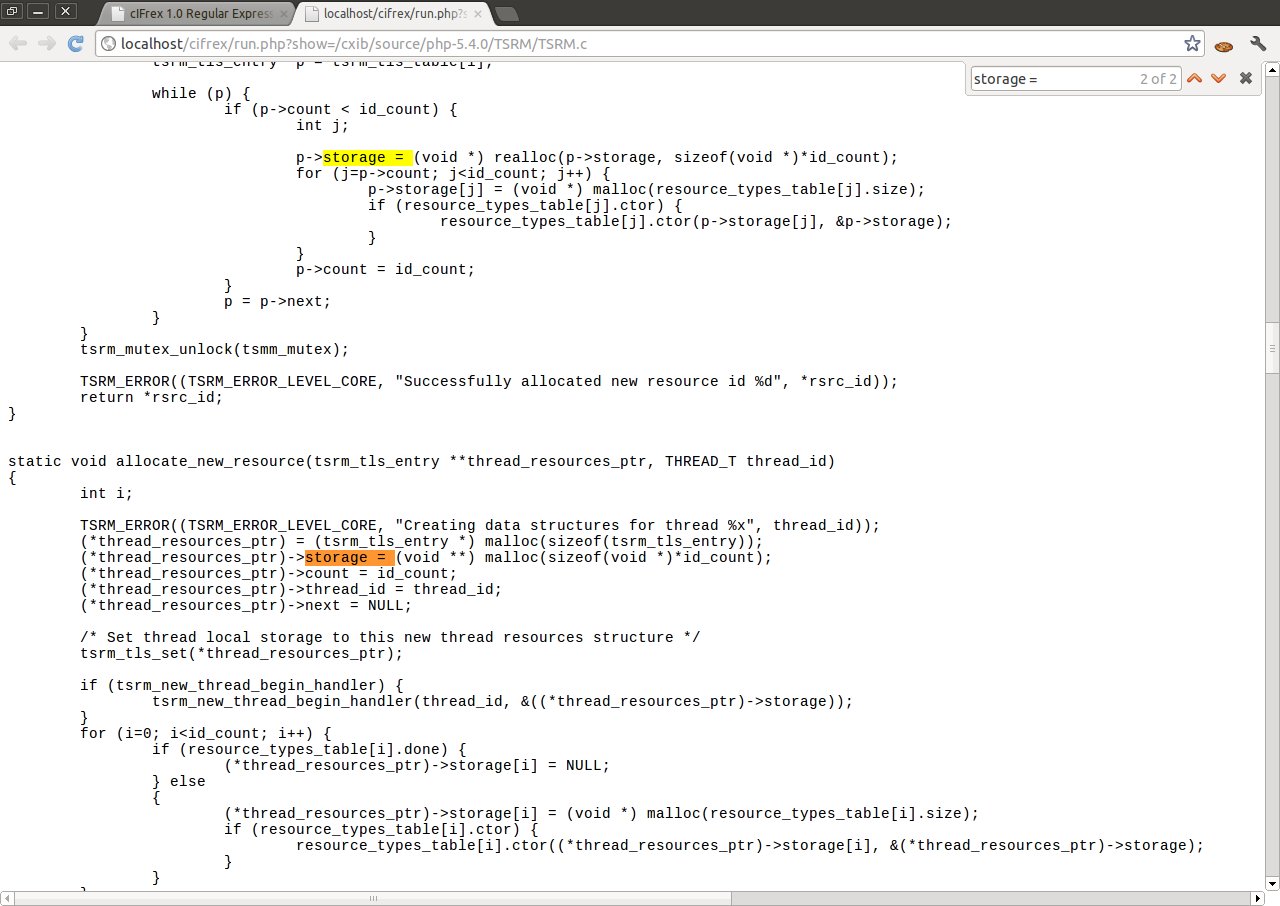
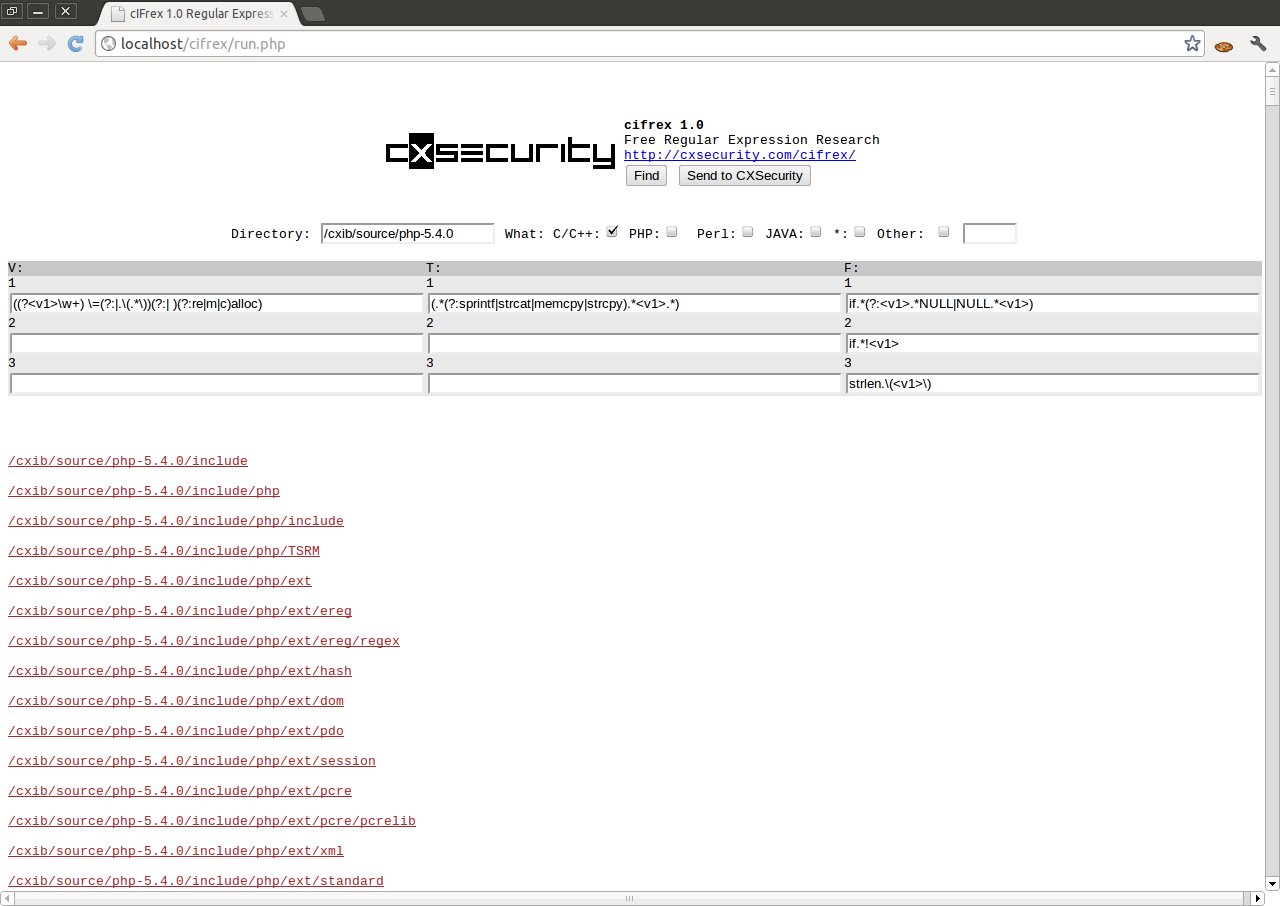
Remember:
- cIFrex helps to search for the mistakes
- the search results does not guarantee the appearance of the susceptibilities
- the more exact the regular expression, the larger probability of the appearance of the susceptibilities
Download
------------------ VERSION 5.x ------------------
02.10.2018 - 5.0 - cIFrex Release - Download
------------------ VERSION 4.x ------------------
21.09.2017 - 4.3 - cIFrex Release - Download
19.09.2017 - 4.2 - cIFrex Release - Download
25.04.2017 - 4.1 - cIFrex Release - Download
------------------ VERSION 3.x ------------------
Git master # git clone https://github.com/MaksymilianA/cifrex.git
Common Weakness Enumeration (CWE)
cIFrex is entirely compatible with the CWE program. This means that each official filter, is equipped with CWE key signature enabling to reach the information about the kind of mistake and the examples of occurrence in other software. CXSecurity is in possession of CWE certificate for the product

cIFrex CVE & CWE Support:
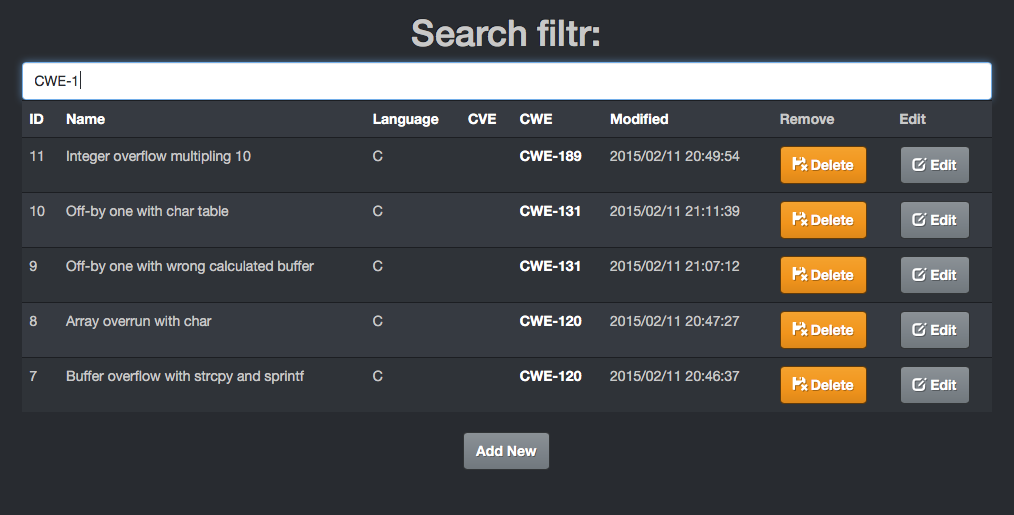
Search: CVE or CWE on cxsecurity.com
History
The idea of program originated in 2010, during the analysis of the code of the library libc of NetBSD system. During the routine use of regular expressions in grep program:
find . -name "*.c"|xargs grep -E'...'
I have come upon the idea of optimizing the use of regular expressions in the analysis of the code. Thanks to which, in several days the first beta version of the cIFrex script originated working with maximum six of regular expressions. After some time I improved the product in order to improve its efficiency. At the beginning of 2011, the first version of the script with maximum nine regular expressions patterns has been created. From that moment, program began to help me in research. Effects can be seen on:
https://cxsecurity.com/research/101
Program helped also in the finding many mistakes in recurrence, which on the detailed analyse proved the susceptibilities of Resource Exhaustion type in the function fnmatch() in the C library systems from the BSD family. This was shifted on the remote possibility of the suspension of Apache server (mod_autoindex)
https://cxsecurity.com/research/98
https://cxsecurity.com/research/95
They are not this all susceptibility which I found with help cIFrex. However in the course of time, I have decided to make the script available to public in 2012 with the hope, that this tool will be useful in the search of mistakes or at least will convince other, that the knowledge of regular expressions pays off.
Let us not rely on the large effects without hard work.
Since 20 October 2013 cIFrex version 2.0 is available. Kacper Rybczynski has joined to cIFrex Team. He has developed and kick off version 2.0 to release.
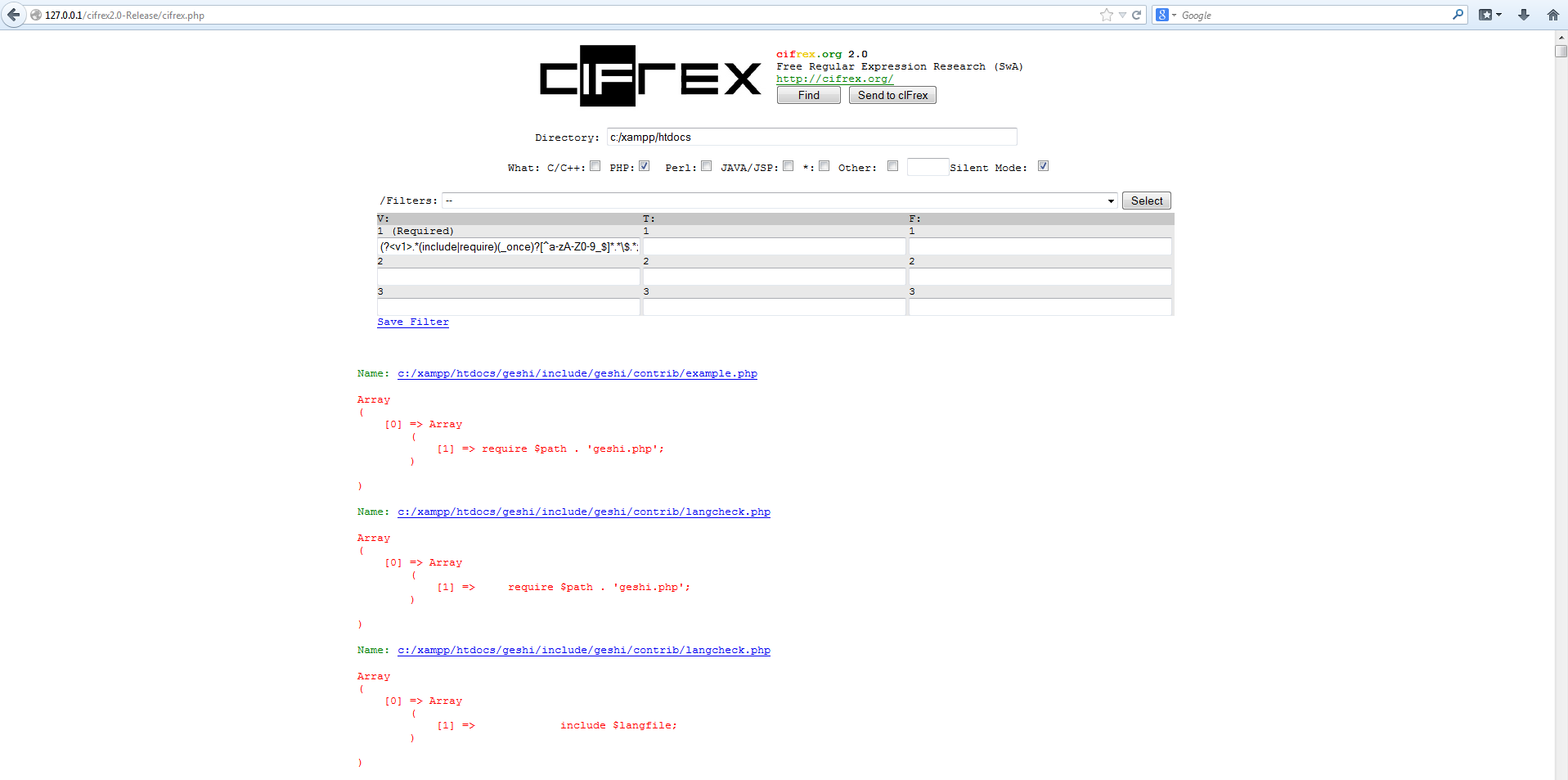

Authors
Maksymilian Arciemowicz
Kacper Rybczynski
Grzegorz Terlikowski
License
cIFrex is completely free. You can use, copy and modify it on the base of BSDv2 license. Remember that you can modify this software and you can become an author of cIFrex by translating it to other language than PHP.
------------ Version 1 and 2 ---------------
Copyright (c) 2017, cIFrex TEAM
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of the CXSecurity nor the
names of its contributors may be used to endorse or promote products
derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY cIFrex TEAM "AS IS" AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL MAKSYMILIAN ARCIEMOWICZ AND KACPER RYBCZYNSKI
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
------------ Version 1 and 2 ---------------
------------ Version 3 ---------------
cIFrex Tool for Static Code Analysis
Copyright (C) 2017 cIFrex Team
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see http://www.gnu.org/licenses/.
------------ Version 3 ---------------

